Saturday, December 25, 2010
Secure Sockets Layer
a protocol developed by Netscape for transmitting private documents via the Internet.


Feed
Is a Term used to describe the process of inserting an object into a device or moving data into another location.


Copyright
Is the exclusive legal right to reproduce, publish, sell, or distribute the matter and form of something like for example a book.


Blog
Is a website were the person created an account can talk about and update information on current events, past events, information on almost everything.

Wiki
Is an open editing database allowing any user to add and update information, create new pages, etc. All done over the internet.


Wesite
Is a computer connected to the internet that maintains a series of web pages on the World Wide Web.


Web 2.0
A term said by Dale Doughert that today many believe to be a word to describe the second generation of the World Wide Web that introduces Internet technologies such as AJAX, Podcasts, RSS feeds, Weblogs, Wikis and other tools that help all users create their own content and help develop a more community driven website.


Uniform Resource Locator (URL)
Short for Uniform Resource Locator, is a form of URI and is a standardized naming convention for addressing documents accessible over the Internet or Intranet.


Social Networking Site
Is a site that brings users together who enjoy similar music tastes or other similar interests.


Really Simple Syndication(RSS)
Is XML-formatted text commonly used for distributing weblogs, news, or other content that is updated frequently.


Portal
The idea of a website or service that offers a broad range of services such as e-mail, games, quotes, search, news, stocks, etc.


Podcast
Is an audio broadcast that is often listened to on a computer or downloaded to a MP3 player such as an iPod.


Mosaic
The first widely used graphical World Wide Web browser developed and first released on April 22,1993 by the NCSA.


Internet Service Provider (ISP)
ISP is a company that provides Internet access to users or subscribers of its service.


Internet Protocol (IP) Address
Is an address of a computer or other network device on a network using IP or TCP/IP.


Hypertext Transfer Protocol (HTTP)
Is a set of standards that allow users of the World Wide Web to exchange information found on web pages.


File Transfer Protocol (FTP)
Is the simplest way to exchange files between computers on the Internet.

Domain
Is a group of computers and devices on a network that are administered as a unit with common rules and procedures. On the internet domains are defined by the IP Address.


Digital Certificate
Is an electronic "credit card" that establishes your credentials when doing business or other transactions on the Web.

Cookie
Is a piece of text stored by a users web browser that can contain anything even personal information.


ActiveX
Is a framework for defining reusable software components that perform a particular function or a set of functions in Microsoft Windows.


Tuesday, December 21, 2010
Urban Legend
Is a form of modern folklore consisting of stories usually believed by their tellers to be true.


Trojan Horse
Is a destructive program that starts off as a application. It doesn't replicate itself but acts as a program that claims to rid your computer of viruses but actually lets them in.


Time Bomb
A malicious program that is programmed to "detonate" at a specific time and release a virus onto the computer system or network.


Teleconferencing
Is a live exchange of verbal information among a group of people in one place and one or more people in another place. Usually far distances from each other.


Tagging
Commonly used in blogs, site authors attach keyword descriptions to identify images or text within their site as a categories or topic.

RDF Summary
An XML format used to syndicate news, blog spots, forum threads and other content among different websites.

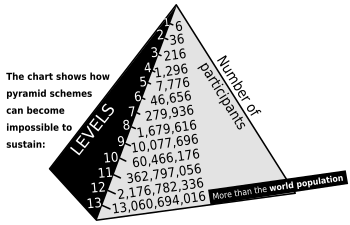
Pyramid Schemes
Is a business model that involves promising participants payment, services or ideals, primarily for enrolling other people into the scheme or training them to take part, rather than supplying any real investment or sale of products or services to the public.

Phishing
Is the act of sending an e-mail to a user falsely claiming to be some type of enterprise for the user to give up private information for identity theft.


Netiquette
Are guidelines for posting messages to online services, and particularly Internet newsgroups.


Logic Bomb
Also called slag code, programming code added to the software of an application or operating system that is set to activate at a certain time. It is similar to a Trojan Horse.


Hoax
In e-mail terminology a hoax is a message which is written for you to open like for example it would probably say "YOU WON A TRIP TO EUROPE" something like that and one of the things that could happen if you open it is that it can delete your hard drive.


filtering
Is deciding which data packets are allowed to be sent and which packets should not be sent.

This software Active Wall is a filtering program.

This software Active Wall is a filtering program.
Window Mail
A Microsoft Windows Vista feature, formally called Outlook Express in previous Microsoft operating systems. Windows Mail better addresses concerns regarding junk e-mail and phishing attacks.


Signature
A digital code that can be attached to an electronically transmitted message that uniquely identifies the sender.


Subscribe to:
Comments (Atom)